Replacing SSH over Cloudflare with Tailscale
I wrote SSH into your private machines from anywhere, for free, using Cloudflare Tunnel in April which led to a lot of discussion on Hacker News. A lot of people started mentioning alternatives (Tailscale, ZeroTier and issues with Cloudflare).
If you like this, you’re gonna love Tailscale https://tailscale.com/ - mmettler
Tailscale has a beta product, Tailscale SSH with 2 significant differences:
- Easier setup: Tailscale SSH is easy to configure (I don’t really need to write the setup steps).
- Less security: Cloudflare Tunnel didn’t replace authentication, but Tailscale SSH does. This means Tailscale could SSH (and access files) into my machine if they wanted to, but Cloudflare can’t. With Cloudflare, I still had to authenticate with my private key.
Steps 🛼
- Install tailscale on client machine (e.g. macOS) and login
- Install tailscale on SSH server (e.g. raspberry pi)
- On SSH server, set up Tailscale to use SSH:
sudo tailscale up --ssh - Get the IP address of the SSH server machine from client machine or Tailscale website
- SSH into the machine:
ssh username@$IP_ADDRESS- If you have Cloudflare WARP: You need to disable it, because that prevented me connecting to my local machines using Tailscale - even though I could still use e.g.
ssh [email protected] -i ~/.ssh/raspberrypithough.
- Optional: shorten SSH command into
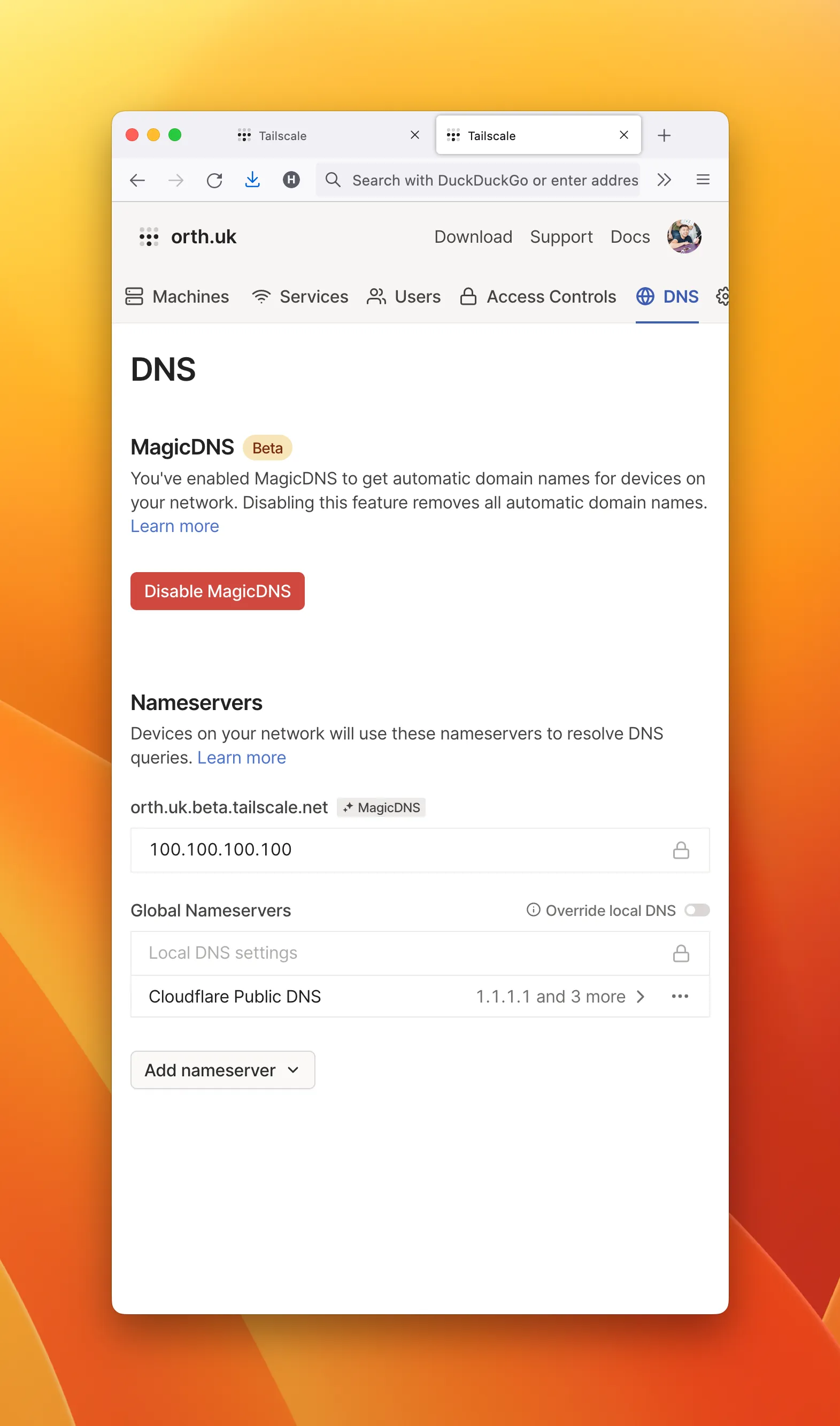
ssh pi- On Tailscale’s DNS admin page,
- select a global nameserver and
- enable MagicDNS
- On Tailscale’s DNS admin page,
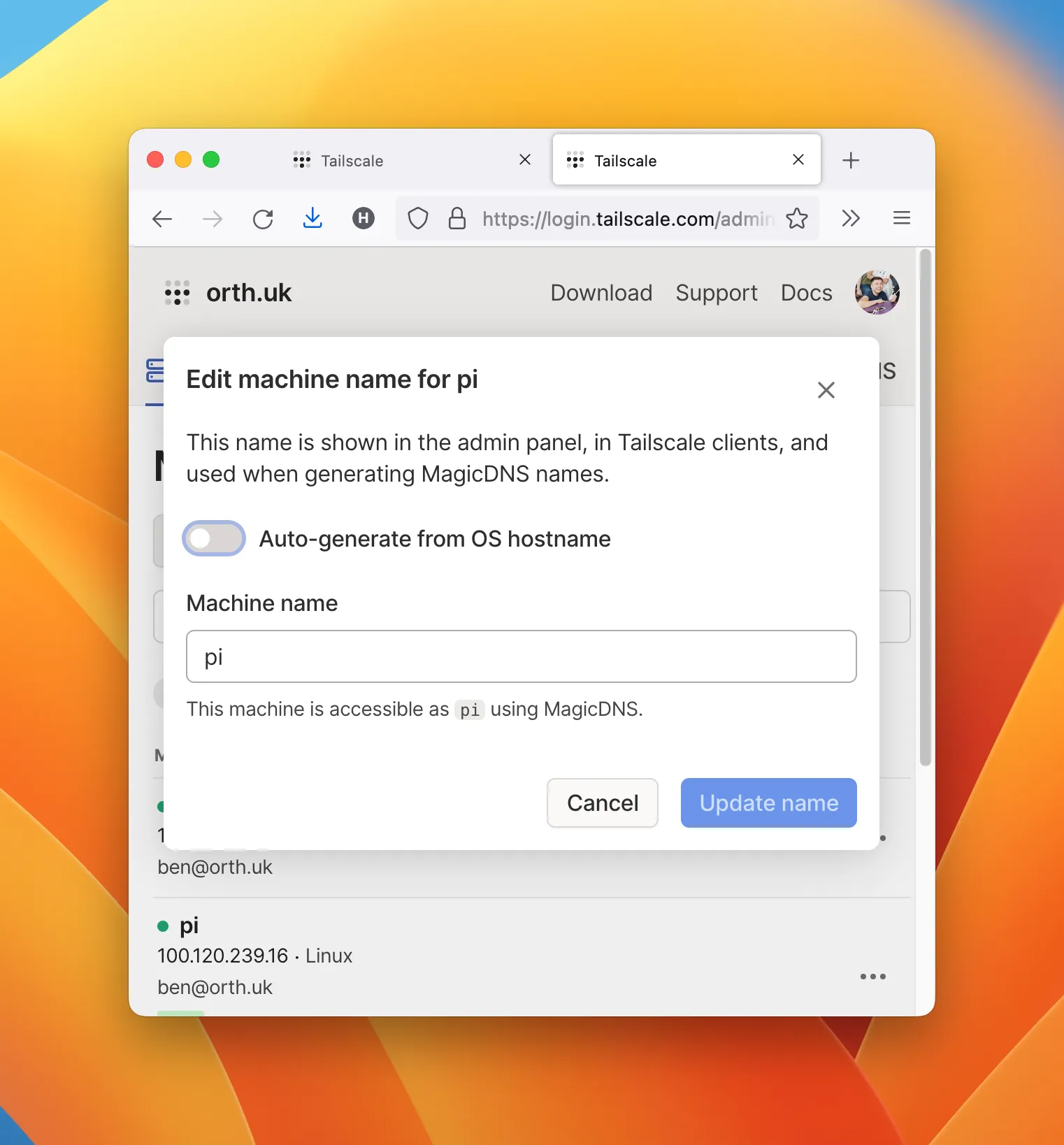
- To SSH into your machine using fewer keystrokes, e.g.
ssh pi, go into Tailscale’s Machines admin page, and “edit machine name”. Disable “auto-generate from OS hostname” and set the machine name.
Benefits 🤙
- No machine passwords or SSH keys needed. Everything is replaced by your Tailscale account or SSO. I can move between laptops by just installing and logging into Tailscale.
- No SSH configuration needed (e.g.
~/.ssh/configand/etc/ssh/sshd_config) - The configuration is so easy, that we can save time and avoid frustration at work. I work at a company with quite a few test devices, and each new person or test device would mean more configuration/setup time. We can:
- see a list of available test devices on the Tailscale website,
- setup developer machines to access these devices using SSO, and
- setup new test devices with 2 commands (install and launch Tailscale).
- We would do all of that whilst avoiding the poor experience with using VPNs and password managers.
Conclusion 🏁
Overall, I think I’m going to stick to Tailscale instead of Cloudflare Tunnel for accessing machines on my home network when away.
Question: what would you do? 😇